Introduction to road map for a vulnerability management team medium
In today’s digital landscape, the stakes are higher than ever when it comes to cybersecurity. With threats evolving at lightning speed, organizations must be prepared to defend their systems against an array of vulnerabilities. This is where a well-structured road map for a vulnerability management team medium becomes essential. By outlining clear strategies and responsibilities, teams can effectively identify, assess, and remediate risks before they escalate into serious breaches.
Creating this road map isn’t just about putting out fires; it’s about building resilience within your organization. A strong vulnerability management team not only safeguards sensitive data but also enhances trust with clients and stakeholders alike. So how do you construct a successful framework that equips your team for success? Let’s dive deeper into the critical components of developing an effective approach to vulnerability management that will keep your organization secure in an unpredictable cyber world.
The Importance of road map for a vulnerability management team medium
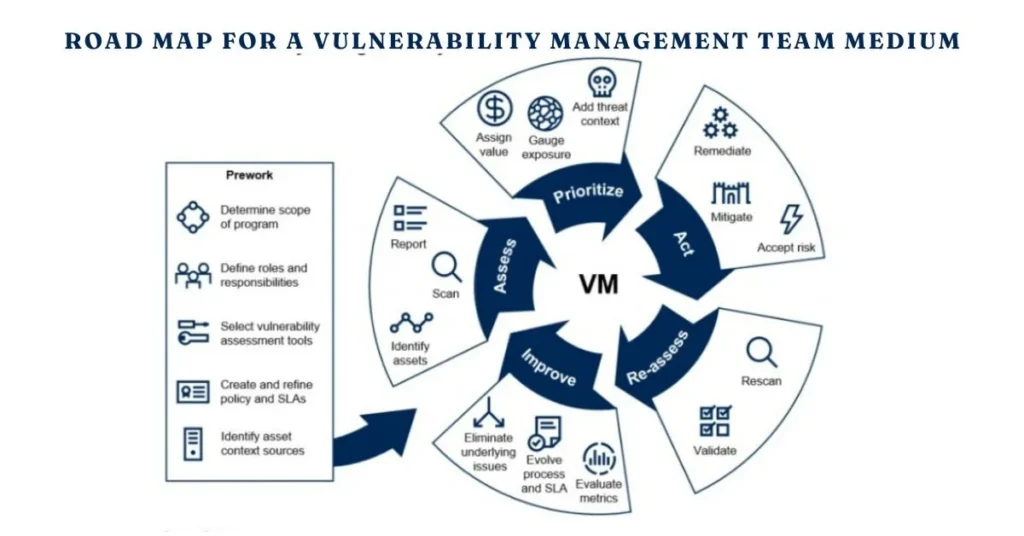
A well-defined road map for a vulnerability management team medium is crucial in today’s digital landscape. It provides direction and clarity, ensuring that all team members are aligned with the organization’s objectives.
With cyber threats evolving rapidly, having a structured approach helps prioritize vulnerabilities based on risk. This not only enhances response times but also optimizes resource allocation.
Moreover, a clear road map fosters accountability within the team. Each member knows their specific roles and contributions towards achieving security goals.
This framework encourages continuous improvement as well. By regularly revisiting and updating the road map, teams can adapt to new challenges and technologies effectively.
An effective road map acts as a blueprint for success in navigating complex security environments.
Building an Effective Vulnerability Management Team
Building an effective vulnerability management team starts with a clear vision. Define the goals and objectives to align your team’s efforts with organizational needs.
A diverse skill set is essential. Include individuals proficient in security analysis, risk assessment, and incident response. This creates a well-rounded unit capable of addressing various vulnerabilities.
Foster open communication within the team. Regular meetings help identify challenges and share insights on emerging threats.
Encourage continuous learning through training sessions or certifications. The cybersecurity landscape evolves rapidly; staying updated is vital for effectiveness.
Establish strong collaboration with other departments like IT, compliance, and operations. A united front enhances threat detection and resolution processes across the organization.
Cultivate a culture of accountability where each member understands their responsibilities while feeling empowered to contribute ideas actively.
ALSO READ: Plutoscreen com: Revolutionizing Digital Operations for Businesses
Roles and Responsibilities of the Team Members
A well-structured vulnerability management team thrives on clearly defined roles. Each member plays a vital part in the collective mission of safeguarding assets.
The team leader oversees operations, ensuring alignment with organizational goals. They coordinate efforts and provide strategic direction.
Security analysts are the detectives of the group. Their task is to identify vulnerabilities through scanning and assessments. They analyze data meticulously to prioritize risks effectively.
Remediation specialists take action based on findings. Their responsibility is implementing fixes and mitigating threats promptly.
Communication experts bridge gaps between technical teams and stakeholders. They ensure everyone understands risks, providing reports that translate complex issues into actionable insights.
Compliance officers monitor adherence to regulations. They’re essential for maintaining standards that protect sensitive information while fostering trust within the organization. Each role contributes uniquely to a comprehensive vulnerability management strategy.
Creating a road map for a vulnerability management team medium Success
Creating a road map for a vulnerability management team requires clear objectives and measurable goals. Begin by identifying critical assets within your organization. This prioritization will help focus efforts on high-risk areas.
Next, define the scope of your vulnerability assessments. Determine which systems, applications, and networks require regular scanning. Establishing a routine ensures nothing falls through the cracks.
Engagement with stakeholders is vital. Collaborate with IT teams to understand their needs and concerns about vulnerabilities. Regular communication fosters cooperation.
Set milestones along your journey to track progress effectively. Use these checkpoints to assess whether you’re on target or need adjustments in strategy.
Incorporate feedback loops into your process for continual improvement. Encourage team members to share insights gained from each assessment cycle, enhancing future efforts and increasing overall effectiveness in managing vulnerabilities.
ALSO READ: Archivebate: Unearthing Stories from Our Digital Footprints
Utilizing Tools and Resources for Efficient Vulnerability Management
Effective vulnerability management relies heavily on the right tools and resources. A robust stack can streamline processes, enhance detection capabilities, and improve response times.
Start by leveraging automated scanning tools. These solutions help identify vulnerabilities across your systems quickly. Automated scans can save time and reduce human error.
Integrate threat intelligence platforms to stay updated on emerging threats. This information allows teams to prioritize vulnerabilities based on real-time risk assessments.
Consider using a centralized dashboard for visibility into all vulnerabilities. Such dashboards provide insights into the status of remediation efforts, making it easier to track progress.
Collaboration tools also play a key role in communication among team members. They facilitate discussions about findings and enable efficient task assignments.
Invest in training resources for your team. Continuous education ensures that everyone stays informed about best practices and evolving threats in cybersecurity.
Measuring Success and Continuously Improving the Process
Measuring success in vulnerability management goes beyond just identifying and patching vulnerabilities. It involves tracking key performance indicators (KPIs) that reflect the health of your security posture.
Regularly assess metrics such as the time taken to remediate vulnerabilities and the percentage of critical issues resolved within a designated timeframe. These numbers provide valuable insights into team efficiency and effectiveness.
Feedback loops are essential for continuous improvement. Gather input from team members after each cycle, discussing what worked well and where challenges arose. This dialogue fosters an environment conducive to growth.
Utilizing automated tools can also enhance measurement processes. Dashboards displaying real-time data allow teams to visualize progress, making it easier to spot trends or bottlenecks quickly.
Stay updated on industry best practices. Implementing lessons learned from other organizations helps refine your strategy over time, ensuring your vulnerability management efforts remain robust and relevant.
ALSO READ: Coyyn.com Digital Business: Revolutionizing DeFi for the Future
Challenges and How to Overcome Them
Vulnerability management teams face numerous challenges. One significant hurdle is the ever-evolving threat landscape. New vulnerabilities emerge daily, making it tough to stay ahead.
Resource constraints can also impede progress. Limited budgets and manpower often lead to prioritization issues. To tackle this, organizations should invest in training and upskilling team members.
Communication barriers within departments may obstruct effective collaboration. Encouraging a culture of open dialogue fosters teamwork and information sharing.
Another common issue is the overwhelming volume of data generated by vulnerability scans. This can result in analysis paralysis, where actionable insights are lost amidst noise. Implementing automated tools with clear reporting features can streamline this process.
Maintaining stakeholder buy-in is essential but challenging. Regularly showcasing successful outcomes helps demonstrate value and keeps leadership engaged in vulnerability management efforts.
Conclusion: The Impact of a Strong Vulnerability Management Team on Cyber
A strong vulnerability management team plays a crucial role in the cybersecurity landscape. Their efforts not only protect vital information but also foster trust among customers and stakeholders. By systematically identifying and addressing vulnerabilities, organizations can significantly reduce their risk exposure.
The impact of an effective vulnerability management strategy extends beyond mere compliance. It enhances resilience against cyber threats, ensuring that businesses can operate smoothly even amidst increasing risks. This proactive approach helps to safeguard sensitive data from breaches while preserving organizational integrity.
Investing time and resources into developing a comprehensive road map for a vulnerability management team paves the way for success in today’s digital environment. Organizations that prioritize this aspect of security will find themselves better equipped to navigate challenges and seize opportunities as they arise.
ALSO READ: Aviyne .com: Simplifying Your Life with Smart Digital Solutions
FAQs
What is “road map for a vulnerability management team medium”?
A road map for a vulnerability management team medium is a structured plan that guides the team in identifying, prioritizing, and remediating vulnerabilities. It outlines clear strategies, roles, and best practices to strengthen an organization’s cybersecurity posture.
Why is a road map essential for vulnerability management?
A road map helps teams prioritize risks, allocate resources efficiently, and stay aligned with organizational goals. It fosters accountability and continuous improvement, ensuring vulnerabilities are managed proactively rather than reactively.
How do you build an effective vulnerability management team?
To build an effective team, start by defining clear goals, assembling individuals with diverse skills, fostering open communication, and providing continuous training. Collaboration with other departments and regular feedback loops are key to success.
What tools can assist in vulnerability management?
Tools like automated scanning systems, threat intelligence platforms, and centralized dashboards are crucial for effective vulnerability management. These tools help streamline processes, enhance detection capabilities, and improve overall response times.
How can organizations measure the success of their vulnerability management efforts?
Success can be measured using key performance indicators (KPIs), such as the time taken to remediate vulnerabilities, the percentage of critical issues resolved, and regular feedback from team members. Dashboards and automated tools also help track progress and identify areas for improvement.